I'd like to focus on cyber security in times of heightened threats today. As we are in unprecedented times, we need to stay alert and be smarter about how we respond.
In the last blog we talked about threat detection and response; this is a revisit to the response. The domain of cyberspace is now more important since we have integrated so much technology into our land, sea, and air operations. These critical pieces of infrastructure are at an elevated risk for attack and are just as much a part of the battlefield.
Cyberspace, now considered by military generals as one of the primary domains of war, is more of a battlefield than ever before. It is not a question of if, but when you will have to respond to online threats. In the last blog post1 in this series, we talked about threat detection and response; this is a more in-depth look at how to respond to online threats and stand your ground on the cyberspace battlefield.
So, where do we begin?
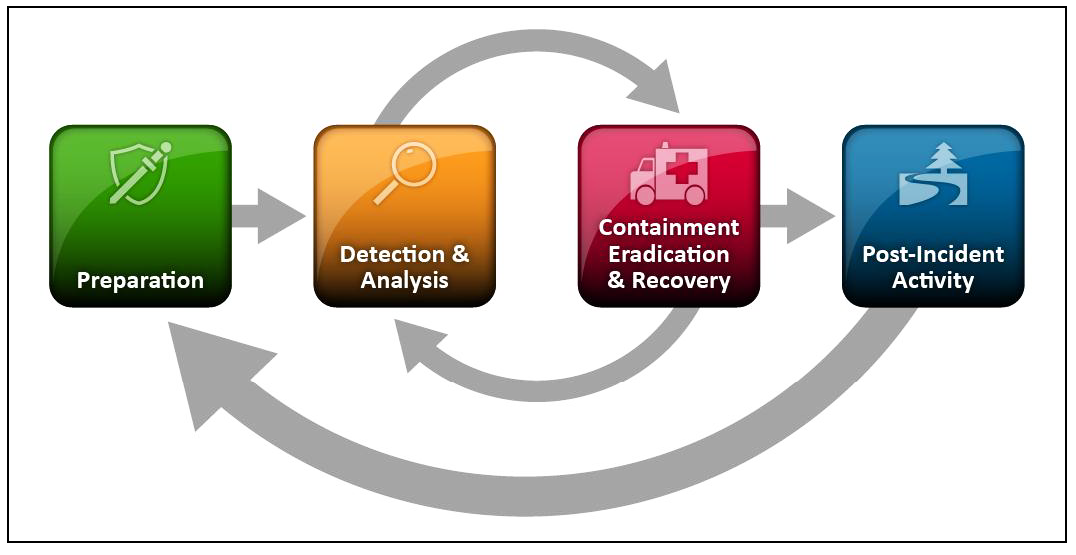
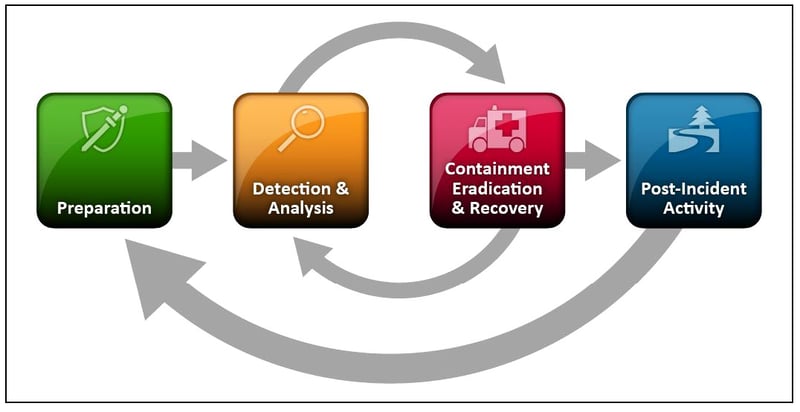
It's crucial that all businesses develop a detailed Incident Response plan for responding to cyberattacks, and there are plenty of resources out there that can help you do so. The NIST Computer Security Incident Handling Guide (SP 800-61)2, the gold standard for guidance in this regard, specifies four areas that should be addressed in this plan:
- Preparation – Planning in advance how to handle and prevent security incidents
- Detection and analysis – Encompasses everything from monitoring potential attack vectors to looking for signs of an incident, to prioritization
- Containment, eradication, and recovery – Developing a containment strategy, identifying the hosts and systems under attack, mitigating the effects, and having a plan for recovery
- Post-incident activity – Reviewing lessons learned and having a plan for evidence retention
|
|
Once you have a detailed Response plan, there are three key cybersecurity areas to watch:
- Identity Security: With the explosion of remote work, securing who's accessing critical data, resources, and apps is a must for organizations. Within this vertical, cybersecurity sub-segments include Identity and Access Management (IAM)3, Privileged Account Management (PAM), and Identity Governance & Administration (IGA). These sub-segments are forecasted to grow by an average compound annual growth rate (CAGR) of 19% between 2021 and 2026.4
- Network Security: Companies in this vertical (i.e business niches where vendors serve a specific audience and their set of needs) are responsible for protecting network integrity, confidentiality, and accessibility from misuse or breaches. Overly permissive networks can cause cyberattacks to move horizontally (i.e. from user to user) once an individual has been compromised. Zero Trust Networks, for example, provide users with access to internal apps, without the need to connect to a company's network or expose those users to the internet. Within this vertical (i.e business niches where vendors serve a specific audience and their set of needs), cybersecurity sub-segments include Zero Trust Network Access (ZTNA), Software-Defined Networking (SDWAN), Network Detection and Response (NDR), Firewall / NGFW / Unified Threat Management (UTM), and Secure Access Secure Edge (SASE). These sub-segments are forecasted to grow by an average CAGR of 24% between 2021 and 2026.5
- Endpoint Security: The multitude of internet-connected devices presents new entry points for hackers, adding challenges and complexity to effectively manage security for firms and individuals. Successful IoT deployments will require multi-layered, end-to-end security that ranges from up front baked-in security requirements to the ongoing management and protection of sensitive machine-generated data. Within this vertical, cybersecurity sub-segments include Endpoint Protection Platform (EPP), Endpoint Detection and Response (EDR), and Data Loss Prevention (DLP). Overall the Endpoint Security vertical is forecasted to grow by an 8% CAGR between 2021 and 2026.6
Digital protection lessons learned during this period could further accelerate the adoption of cybersecurity services, even with the ever shifting landscape. In our view, recent financial commitments to thwart cybercriminals can form tailwinds for cybersecurity companies in 2022 and strengthen the long-term investment case for the cybersecurity theme overall.
Lastly, be sure to check CISA7(Cybersecurity & Infrastructure Security Agency) to stay up to date with federal guidelines.
Citations:
1Harrylal, D. Cloud security series - Part 3: Threat detection and initial response in the cloud, 3-GIS, 2022
2Computer Security Incident Handling Guide, SP 800-61, Rev 2, National Institute of Standards and Technology, 2012 https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-61r2.pdf
3Harrylal, D. Cloud security series - Part 2: The importance of identity access management, 3-GIS, 2022 https://blog.3-gis.com/blog/the-importance-of-identity-access-management-to-cloud-security
4Metric derived from average CAGRs featured in the following sources: Technavio, "Privileged Access Management Solutions Market by Deployment and Geography - Forecast and Analysis 2022-2026," January 2022., https://www.technavio.com/report/privileged-access-management-solutions-market-industry-analysis, Mordor Intelligence, "Identity Governance And Administration Market - Growth, Trends, Covid-19 Impact, and Forecasts (2022 - 2027)," January 2022, https://www.researchandmarkets.com/reports/5239400/identity-governance-and-administration-market, Technavio, "Consumer Identity and Access Management (IAM) Market by Deployment and Geography - Forecast and Analysis 2022-2026," December 2021. https://www.technavio.com/report/consumer-iam-market-industry-analysis
5Metric derived from average CAGRs featured in the following sources: Markets and Markets, "Zero Trust Security Market by Solution Type (Data Security, Endpoint Security, API Security, Security Analytics, Security Policy Management), Deployment Type, Authentication Type, Organization Size, Vertical, and Region - Global Forecast to 2026," February 2021, https://www.marketsandmarkets.com/Market-Reports/zero-trust-security-market-2782835.html, Research and Markets, "SD-WAN - Global Market Trajectory & Analytics," April 2021, https://www.researchandmarkets.com/reports/5030575/sd-wan-global-market-trajectory-and-analytics, Market Growth Reports, "Global Network Detection and Response (NDR) Market Growth (Status and Outlook) 2021-2026," July 2021, https://www.marketstudyreport.com/reports/global-network-detection-and-response-ndr-market-growth-status-and-outlook-2021-2026, Expert Market Research, "Global Unified Threat Management Market: By Component: Hardware, Software, Virtual; By Service: Consulting, Support & Maintenance, Managed UTM; By Deployment Mode; By Company Size; Regional Analysis; Historical Market and Forecast (2017-2027); Market Dynamics; Competitive Landscape; Industry Events and Developments," 2021, https://brandessenceresearch.com/technology-and-media/unified-threat-management-market-size, Markets and Markets, "Secure Access Service Edge (SASE) Market with COVID-19 Impact Analysis, by Offering (Network as a Service and Security as a Service), Organization Size (SMEs and Large Enterprises), Vertical, and Region - Global Forecast to 2026," August 2021, Global X Analysis, https://www.researchandmarkets.com/reports/5414956/secure-access-service-edge-sase-market-with
6Mordor Intelligence, "En dpoint Security Market - Growth, Trends, Covid-19 Impact, and Forecasts (2022 - 2027)," January 2022. https://www.mordorintelligence.com/industry-reports/endpoint-detection-and-response-market
7“Shields Up, Cybersecurity and Infrastructure Security Agency (CISA), 2022 https://www.cisa.gov/shields-up