Cloud environments change fundamental assumptions in how to perform threat detection and response. A growth of new infrastructure and deployment models results in new environments with new security models and attack surfaces. In particular, shared responsibility with a cloud service provider creates potential threat visibility gaps in the attack lifecycle.
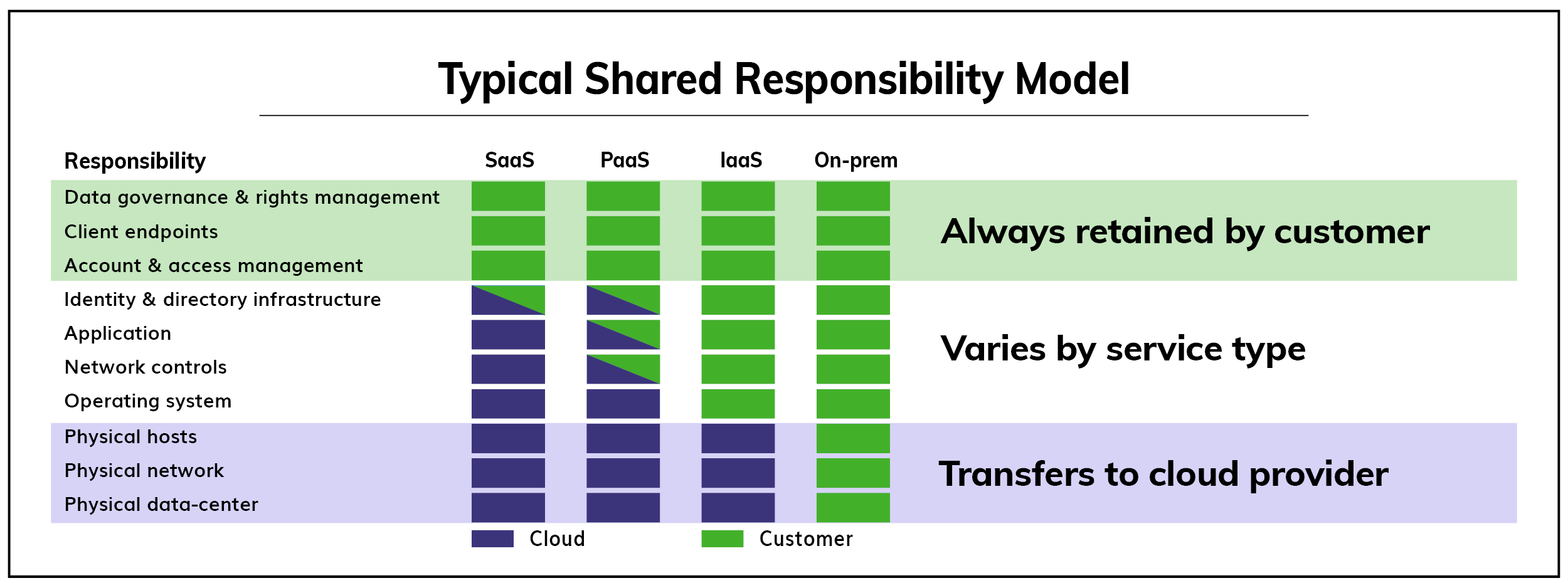
Shared responsibility model
The dynamics of the cloud are different. Let’s take infrastructure-as-a-service (IaaS) as an example. In this case, virtual data centers replicate existing internal data centers. More specifically, physical segregation of hardware is not possible and requires hypervisor-level1 capabilities to create security zones.
Further, when choosing between managing the infrastructure in a private or public cloud, most organizations find themselves with a hybrid cloud, a combination of the private and public cloud with shared resources and distribution components. Usually, the critical back-end infrastructure is private, and the access is public.
In this environment, the highly dynamic inventory of cloud workloads means systems come and go in seconds. A heavy focus on automation amplifies the potential for human error in system configurations. Everything in the cloud is moving to an API data access method, and traditional approaches to monitoring traffic flow no longer apply. Because of these dynamics, confidential information can be exposed to other users or to the cloud service provider because no control is provided over existing hardware. Controls must be applied using encryption and external key management designed for virtual environments.
Most critically, the introduction of multiple access and management capabilities creates variability that adds significant risk to cloud deployments. It is difficult to manage, track, and audit administrative actions when those users can access cloud resources from inside or outside the corporate environment.
What your Cloud Security Posture Management tool may be missing
According to the IBM Data Breach Report 20202, it takes organizations, on average, 280 days to discover and contain a breach. Considering how essential the cloud has become for businesses, and how quickly it evolves, 280 days is more than enough time to cause significant damage.
Focusing on maintaining hygiene through compliance and configuration management, without monitoring for new threats, leaves organizations completely exposed. It's like spending time making sure the doors are locked without considering putting up security cameras. After all, there is no such thing as “perfect” protection, and a malicious actor just needs one loophole to exploit.
Given the added complexities of the cloud (accelerated development pace, distributed environments, diversity in microservices, constantly changing network activities), proactive threat detection must be a component of a comprehensive strategy. As more and more users and workloads are added to cloud environments, continuously monitoring behavior for suspicious activities is critical. This means a combination of static rule and machine-learning-based security policies; as well as user activity monitoring.
Let’s take a look at four ways to quickly detect risks and prevent incidents across cloud environments.
1. High Fidelity Threat Intelligence
There are numerous threat detection solutions on the market today. But a tool's ability to effectively identify and surface risks is only as good as its data source. For many solutions, this means a disparate assortment of cloud service provider logs and open-source feeds.
2. Network Threat Detection
In fall 2020, the Palo Alto’s Unit 42 cloud threat research team found that cryptojacking affects at least 23% of organizations globally3 that maintain cloud infrastructure, a slight improvement over 28% of organizations in 20194. This shows the challenges organizations face in effectively detecting threats in their cloud environments.
3. Network Anomaly Monitoring
While traditional rule or signature-based policies can prevent known bad behaviors from continuing, they can't protect against zero-day attacks and other types of advanced, persistent threats (APTs).
4. User Entity Behavior Analytics
The final piece of an effective threat detection strategy should focus on user behavior. Users who access cloud environments can pose a significant threat if not continuously monitored for unusual activities that could signal the possibility of credential or account compromise, as we saw on average 280 days to notice. Similar to the network anomaly policies, fine-grained controls enable users to train the machine learning model to minimize false positives and negatives, as well as customize alert disposition. Users can also specify policy-specific trusted lists to avoid getting anomaly alerts from resources that are known to be used for things like penetration testing.
Strategic Security
In an ideal world your strategy would be designed to help you build secure, high-performing, resilient, and efficient infrastructure for your applications. You would want world-class security experts who monitor your infrastructure and also build and maintain your broad selection of innovative security services, which can help you simplify meeting your own security and regulatory requirements. Here's what to look for in security services and solutions that are focused on delivering the following key strategic benefits critical to helping you implement your organization’s optimal security posture:

Key takeaways
In most attacks, the method of initial intrusion is cloud specific, but the attack behaviors within those cloud environments are consistent with behaviors found in private cloud and physical data centers.
This is because all attacks must follow a certain attack lifecycle to succeed. Preventing a compromise is increasingly difficult but detecting the behaviors that occur are not. More importantly, when an attack is carried out in hours rather than days, the time to detect becomes critically more important.
A key takeaway from the shared responsibility model is that regardless of the data center model deployed – infrastructure, platform, or software as a service – the enterprise organization is always responsible for data, endpoints, accounts, and access management.
Managing access
While cloud service providers need to ensure their own access management and controls that limit access to cloud tenant environments, tenants themselves must assume this can be compromised and focus on learning the who, what, when and where of access management.
Properly assigning user access rights helps by reducing instances of shared credentials so cloud tenants can focus on how those credentials are used. Resource access policies can also reduce opportunities for movement between the cloud service provider infrastructure and cloud tenants.
Detect and respond
When it comes to cloud and on-premises monitoring, it is necessary to monitor both as well as determine how to correlate data and context from both into actionable information for security analysts. Monitoring cloud-deployed resources by cloud tenants is essential to increase the ability to detect lateral movement from the cloud service provider infrastructure to tenant environments and vice versa. Coordinating with the cloud service provider – as well as cloud service provider coordination with cloud tenants – can provide a powerful combination of information that can increase the likelihood of detecting post-compromise activities.
More importantly, visibility into attacker behaviors is dependent on the implementation of proper tools that can leverage cloud-specific data.
Security operations
Knowing and managing the infrastructure as a part of due diligence should help to identify systems and operations that are compromised by malware implants like those used in some online operations.
Changes to production systems can be difficult to detect. But when visibility is available in the cloud infrastructure, it is much easier to detect attacker behaviors in compromised systems and services that are clearly operating outside of expected specifications. Ideally, security operations teams will have solid information about expectations for that infrastructure, so deviations from normal activity are more likely to identify malware and its activity, enabling a proper response to ensure continued security in your organization.
Check back next month for the fourth blog in this series which will cover cloud security threat response techniques and methodologies more in detail.
Citations:
1 A hypervisor is a program used to run and manage one or more virtual machines on a computer.
2 Cost of a Data Breach Report, IBM, 2020 https://www.ibm.com/security/data-breach
3 Cloud Threat Report 2H 2020, Palo Alto Networks, 2020 https://www.paloaltonetworks.com/prisma/unit42-cloud-threat-research
4 Cloudy with a Chance of Entropy, Palo Alto Networks, 2019 https://www.paloaltonetworks.com/resources/research/unit42-cloud-with-a-chance-of-entropy
.png)