 $74.6 billion. That’s the estimated amount to be spent on cloud IT infrastructure in 2021, according to Statista1. The explosive growth of cloud services is creating a unique set of challenges for enterprises seeking improved ways to secure their data.
$74.6 billion. That’s the estimated amount to be spent on cloud IT infrastructure in 2021, according to Statista1. The explosive growth of cloud services is creating a unique set of challenges for enterprises seeking improved ways to secure their data.
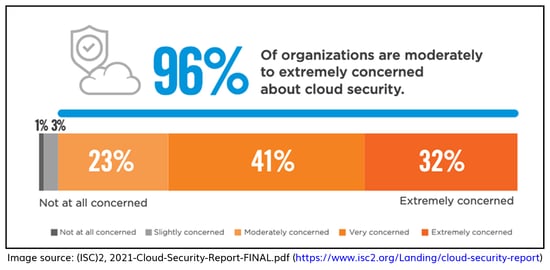
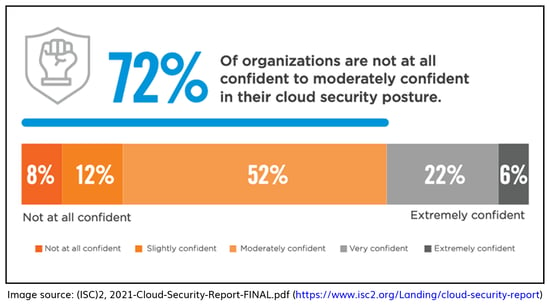
Security remains a top concern for IT decision-makers, but many are not fully prepared. The cloud is much more than just technology: it’s an evolution in the way businesses operate and leverage technology
Why cloud security is required
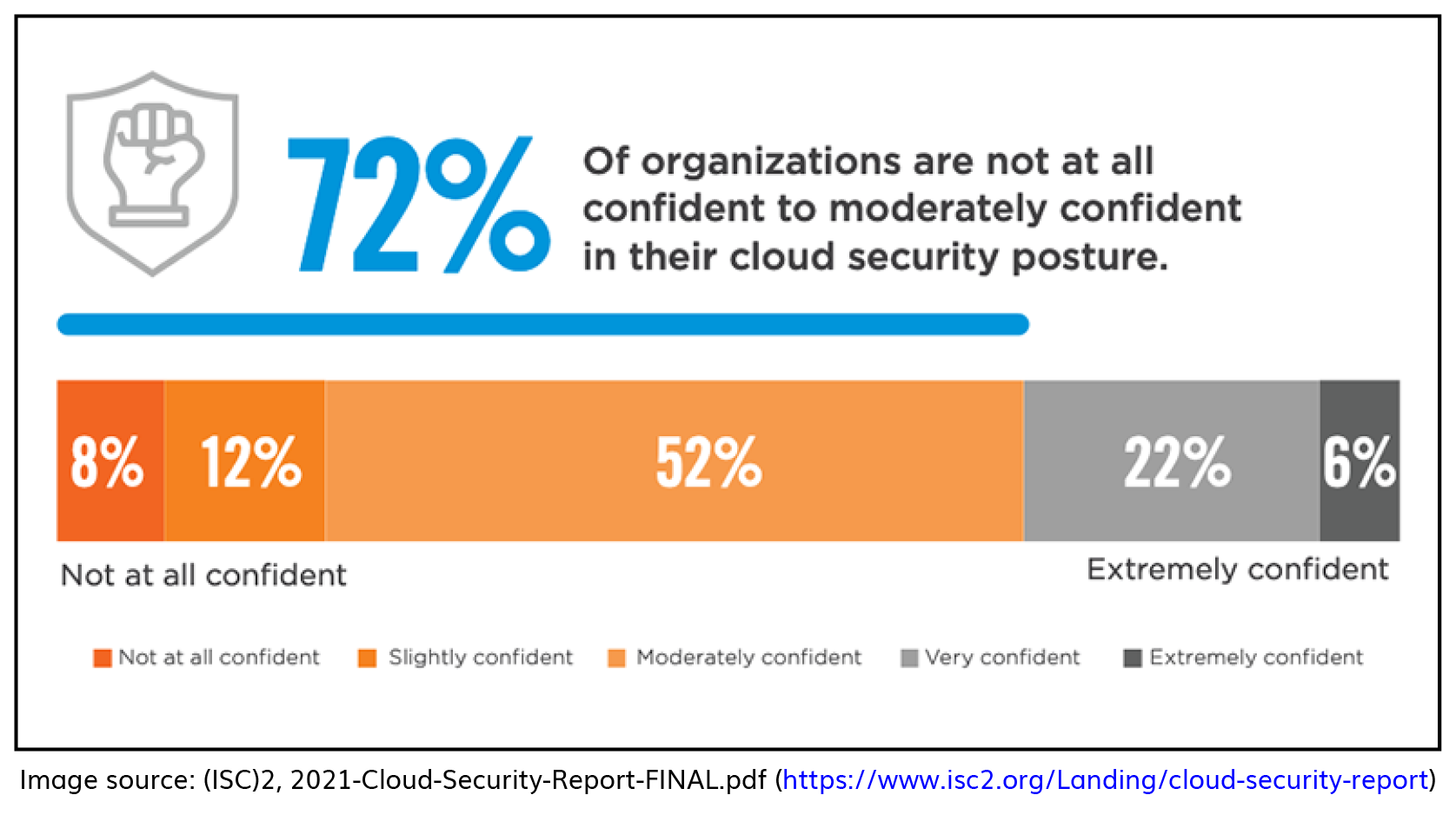
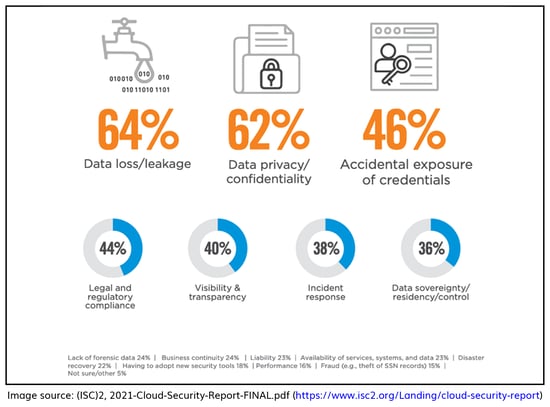
The mass adoption of cloud technology combined with an ever-increasing volume and sophistication of cyber threats is what drives the need for cloud security. Reflecting on the security risks of adopting cloud technology, as reflected in the graphic above, failure to mitigate them can come with significant implications.
But it’s not all negative, cloud security can also offer significant benefits. Let’s explore why cloud security is a critical requirement.
 Cyber security threats continue to increase
Cyber security threats continue to increase
A driving force for secure cloud practices is the ever-increasing threat from cybercriminals – both in volume and sophistication. The 2021 Thales Global Cloud Security Study2, commissioned by Thales and conducted by 451 Research, reports that 40% of organizations have experienced a cloud-based data breach in the past 12 months. An increase of 12% since 2019 according to this ISC report3.
Presenting data breaches and data loss
A consequence of these increased cyber threats is the acceleration in frequency and volume of data breaches and data loss. A loss or breach of data can have significant legal, financial, and reputational implications. IBM now estimates the average cost of a data breach at $4.24 million USD in its latest report4.
Remote work during the pandemic has contributed to this as a factor and as this becomes the new normal, companies are having to slightly pivot strategy.
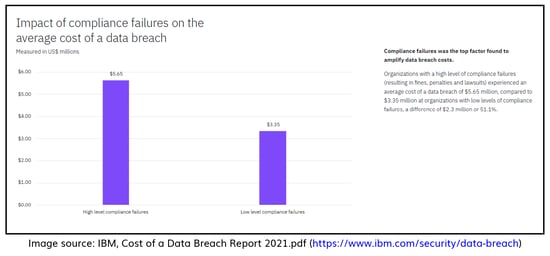
Avoid compliance violations
We’ve already mentioned how cloud security carries the risk of compliance violations. To demonstrate the implications of non-compliance, you need only to observe Germany’s federal privacy watchdog, who recently handed 1&1 Telecommunications a €9.55 million fine for violating the EU’s General Data Protection Regulation (GDPR).
 Maintaining business continuity
Maintaining business continuity
Good cloud security helps maintain your business continuity, by protecting against threats like a denial-of-service (DDoS) attack. Unplanned outages and system downtime interrupt your business continuity and impact your bottom line. A Gartner research study5 estimates this downtime cost at an average of $5600 per minute.
As bad actors and security threats continue to evolve, so must IT security solutions.
To keep up, we must all rethink strategies with a next-generation cloud security approach: one that encompasses cloud-native capabilities and addresses the unique needs of the cloud-based environment.
This is the first of a series of five blogs elaborating on the key pillars of cloud security. Later in this series, we will explore distributed cloud adoption, hybrid/multi-cloud adoption, and IoT-Cloud compatibility. Other areas to consider for cloud security include implementing zero trust network access (ZTNA), serverless technology and applications of artificial intelligence (AI) and machine learning (ML) in cloud architecture, specifically as it relates to security. These will become greater factors as the technology continues to evolve.
The challenge for cloud users, for now, is to assume greater responsibility in protecting their cloud assets and resources. The next blog in the series, “The importance of identity access management”,
1 https://www.statista.com/statistics/503686/worldwide-cloud-it-infrastructure-market-spending/
2 https://www.securitymagazine.com/articles/96412-40-of-organizations-have-suffered-a-cloud-based-data-breach
3 https://www.isc2.org/Landing/cloud-security-report/Thank-you
4 https://www.ibm.com/security/data-breach
5 https://blogs.gartner.com/andrew-lerner/2014/07/16/the-cost-of-downtime/